Digital Machining
The PoliMill course is aimed at staff and engineering department managers of manufacturing companies involved in milling. Participants will use a modern, digital workflow to design and implement a milling cycle. The goal is to lower the barrier to entry into the world of Digital Machining and Industry 4.0 applied to machining.
Il corso permette l’utilizzo di software allo stato dell’arte del Digital Machining come Sandvik Coromant ToolGuide®, Siemens NX®, CGTech Vericut® e Bruker Alicona MetMaX® mettendo a disposizione i PC ai partecipanti.
LESSONS
Lesson 1: Introduction to the world of chip removal
This lesson introduces the basics needed to approach the industrial world of chip removal with a focus on milling theory.
Lesson 2: Tool Holder
This lecture introduces tool gripping systems, the various types of standardized spindle interfaces, types of clamping and their characteristics.
Lesson 3: Coolant fluids
This lecture introduces the theoretical basis of lubrorefrigeration, the distinction between the various types of lubrorefrigeration, their characteristics and applicability.

Lesson 4: Set up operations on CAM
This lesson introduces the basics of being able to properly set up the basic operations of the milling process, such as: face milling, contouring and making pockets from solid. The Siemens NX® CAM program will be used at this juncture.
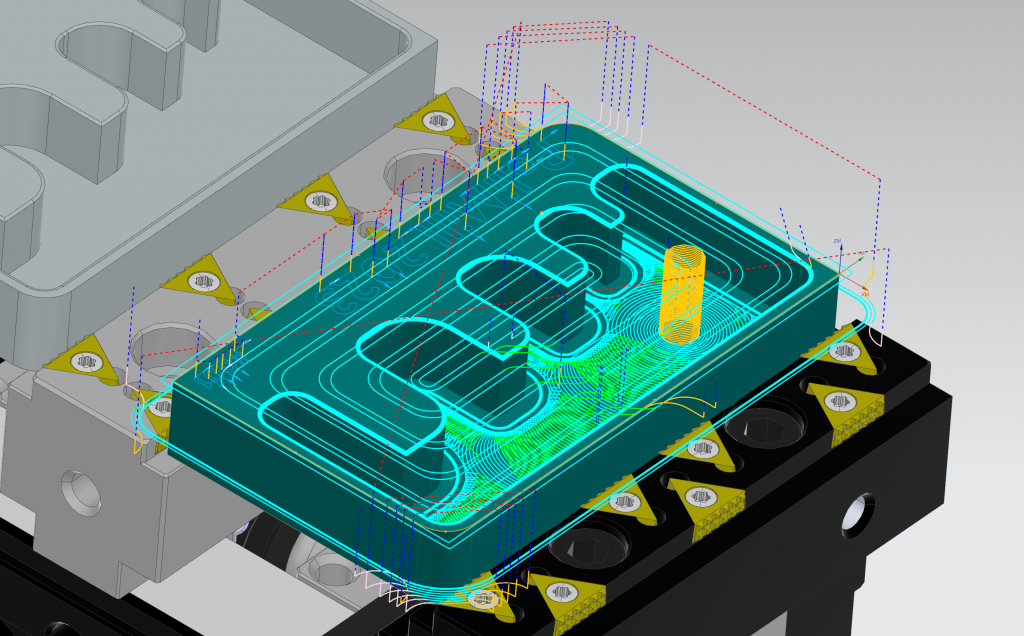
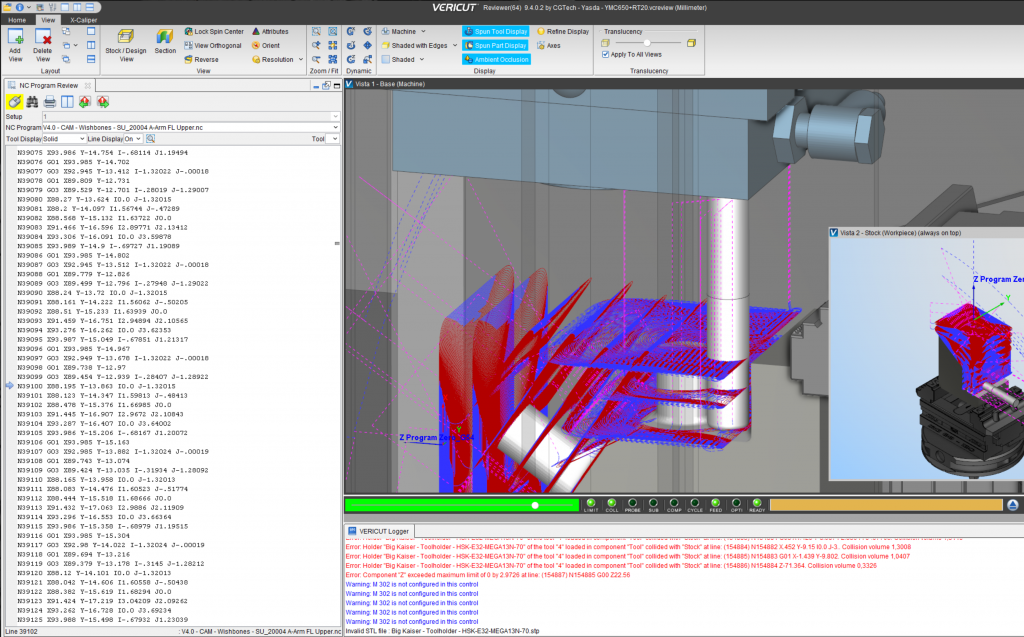
Lesson 5: Simulating Processes with CGTech VERICUT®
In this lesson we introduce the basics in order to fully understand what functions and capabilities a high-level simulator like VERICUT® can offer. Starting with process verification and arriving at the optimization of the process parameters themselves.
Lezione 6: Soluzioni di misura innovative per la produzione
In questa lezione viene presentata la tecnologia di misura ottica 3D. Vengono presentati i vantaggi dell’adozione di una tecnologia senza contatto che permette misurazioni precise e immediate anche dove le tecnologie tradizionali non arrivano.

Lezione 7: La Cybersecurity nel mondo delle macchine utensili
In questa lezione si introducono le buone pratiche che ognuno dovrebbe seguire per preservare i propri dati da attacchi esterni. Nella seconda parte infine vengono presentate le vulnerabilità delle macchine utensili ad attacchi hacker tramite i protocolli di comunicazione.